A few days after uncovering the CCleaner malware attack, researchers found out that some high-profile technology companies were the main target of the attackers.
Last Monday, news of the CCleaner malware attack made headlines after threat analysts from Cisco Talos found a security breach on the server which handles the download of CCleaner Version 5.33. Apparently, the breach enabled the unknown group of hackers to replace the legitimate program with a copycat malware version.
That time, the researchers assured everyone that there’s no second stage malware used to execute the massive attack and that affected users, around 2.3 million users worldwide, can just simply update their downloaded V5.33 to V5.44 or higher to get rid of the malicious program.
#CiscoTalos found #CCleanerMalwareAttack to be bigger than what they first thought!Click To TweetHowever, a thorough analysis of the alleged hackers’ command-and-control or C2 server, where the CCleaner malware was connected, gave researchers from Talos enough evidence of the existence of a second payload that was only delivered to a particular set of computers based on local domain names.
On a recent report released by Cisco Talos, they said:
“During our investigation we were provided an archive containing files that were stored on the C2 server. Initially, we had concerns about the legitimacy of the files. However, we were able to quickly verify that the files were very likely genuine based upon the web server configuration files and the fact that our research activity was reflected in the contents of the MySQL database included in the archived files.”
CCleaner Malware Attack: The High-Profile Targets
According to the analysts from Talos, during their investigation, they were provided with an archive containing files that were stored on the CCleaner malware attack C2 server. Upon checking, the files were found to be legitimate and based upon the server configuration files. The archive files also showed Cisco’s research activity in the contents of the included MySQL database.
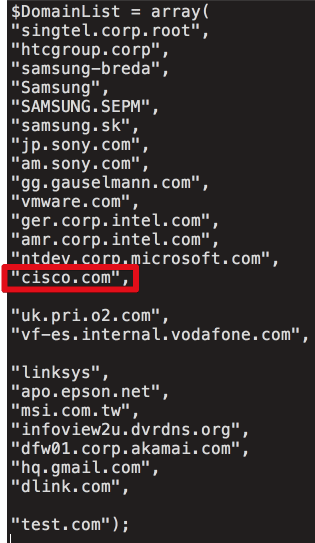
“In analyzing the delivery code from the C2 server, what immediately stands out is a list of organizations, including Cisco, that were specifically targeted through delivery of a second-stage loader. Based on a review of the C2 tracking database, which only covers four days in September, we can confirm that at least 20 victim machines were served specialized secondary payloads. Below is a list of domains the attackers were attempting to target,” the team added.
The predefined list mentioned in the C2 server confirms that the CCleaner malware attack was specifically designed to find computers within the networks of some major technology companies where the second payload will be delivered. The list includes:
- Microsoft
- Cisco
- Intel
- Samsung
- Sony
- HTC
- Linksys
- D-Link
- Akamai
- VMware
Further investigation into the database uncovered a list of nearly 700,000 backdoored machines infected by the first stage payload of the malicious CCleaner version, plus around 20 machines that were already infected by the secondary payload that will be used to infiltrate those systems deeper.
Apparently, the alleged 20 machines were specifically chosen by the hackers based on their Domain name, IP address, and Hostname. Because of this, researchers were convinced that the secondary payload would be used for espionage.
Researchers from Kaspersky Labs said that the CCleaner malware attack shares some codes with the hacking tools used by the China-based hacking group Axiom, which is also known as APT17, Group 72, DeputyDog, Tailgater Team, Hidden Lynx or AuroraPanda.
In addition to the said information, Talos also noted that one configuration file on the attackers’ server was set to China’s time zone, an apparent hint that the source of the CCleaner malware attack could be China.
Unfortunately, removing the Avast’s software from the infected machines would not be enough to get rid of the secondary payload malware from the tech companies’ networks. Instead, researchers strongly suggest that the said companies restore their systems from the backup version before the installation of the CCleaner malware version.




Comments (0)
Most Recent