If you’re one of the millions of individuals who downloaded the CCleaner application on your computer between this last August 15th and September 12th, be warned–your computer was potentially infected by the CCleaner malware.
Cybersecurity experts from Cisco Talos, the threat intelligence group of Cisco, reported that unidentified hackers have successfully infiltrated the download servers of Avast that let users download the CCleaner app and replaced it with what they dubbed as the CCleaner malware.
A part of the threat intelligence report that the Talos researchers published read:
“Talos recently observed a case where the download servers used by software vendor to distribute a legitimate software package were leveraged to deliver malware to unsuspecting victims. For a period of time, the legitimate signed version of CCleaner 5.33 being distributed by Avast also contained a multi-stage malware payload that rode on top of the installation of CCleaner.”
Avast, a company which focuses on developing antiviruses and other security applications for Microsoft Windows, MacOS, Android, and iOS, owns CCleaner. CCleaner is an application that allows its users to conduct routine maintenance on their computer systems.
According to the Piriform website, the creator of CCleaner acquired by Avast in July of this year, the CCleaner application has over 2 billion downloads worldwide as of November 2016.
The company also boasts that per month, the application can clean over 35 million GB of space–or about 7 billion selfies-worth of data.
Supply Chain Attacks
According to Talos, the hacking of the CCleaner hack is another example of supply chain attack.
“Supply chain attacks are a very effective way to distribute malicious software into target organizations. This is because with supply chain attacks, the attackers are relying on the trust relationship between a manufacturer or supplier and a customer. This trust relationship is then abused to attack organizations and individuals and may be performed for a number of different reasons.”
A similar kind of attack, the Nyetya attack, was staged earlier this year and affected many organizations inside of Ukraine and multinational corporations operating in the said country. Further investigations into the case lead the Talos researchers to a “supply chain-focused attack at M.E.Doc software that delivered a destructive payload disguised as ransomware.”
Reports from Ukraine Cyber police confirmed that the effects of the supply chain attack was broad reaching and compromised over 2000 companies in Ukraine alone.
Uncovering the CCleaner Malware
Threat analysts from Talos reported that the CCleaner malware was just detected last September 13th. The malicious version of the application was said to contain multi-stage malware payload that steals data from compromised computer systems and sends them back to the remote command-and-control servers of the hackers.
“On September 13th, 2017, while conducting customer beta testing of our new exploit detection technology, Cisco Talos identified a specific executable which was triggering our advanced malware protection systems,” says Talos.
Closer inspection of the said malicious executable led the security experts to an installer for CCleaner v5.33. The installer was said to be delivered to endpoints by legitimate download servers.
“During the installation of CCleaner 5.33, the 32-bit CCleaner binary that was included also contained a malicious payload that featured a Domain Generation Algorithm (DGA) as well as hardcoded Command and Control (C2) functionality. We confirmed that this malicious version of CCleaner was being hosted directly on CCleaner’s download server as recently as September 11, 2017.”
Furthermore, it was also discovered that the affected version (v5.33) was released and distributed starting August 15th. On September 12th, Piriform released the v5.34 of the application. This led experts to conclude that the CCleaner malware was actively being released between those two dates.
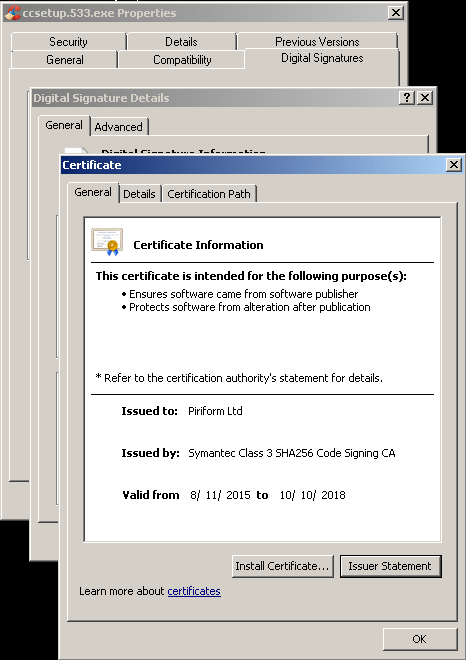
The malicious version was also found to have been signed using a valid certificate that was issued to Piriform Ltd by Symantec and is valid through October 10th, 2018.
In a statement released by Piriform yesterday, Paul Yung, Vice President of Products at Piriform, was quoted as saying:
“All of the collected information was encrypted and encoded by base64 with a custom alphabet. The encoded information was subsequently submitted to an external IP address 216.126.x.x (this address was hardcoded in the payload, and we have intentionally masked its last two octets here) via a HTTPS POST request.”
The CCleaner malware was reportedly programmed to collect user data which includes computer name, installed software (including Windows update), list of running processes, IP and MAC addresses, plus additional information such as programs and applications running with admin privileges or whether it is a 64-bit system.
Right now, all potentially affected users are strongly recommended to update their CCleaner software to version 5.34 or higher immediately!












Comments (0)
Most Recent