For years, security experts have been working extra hard to fight off cyber criminals and their often vicious attacks–one of which is spreading ransomware to extort money from their victims.
Ransomware is a royal pain in the neck.
It can be used to target any victim, from innocent individuals to large enterprises, hospitals, and financial institutions. No one is safe from it.
Just imagine having all your precious computer files or your whole computer system being held hostage. All your work and personal data threatened to be exposed or encrypted forever if you failed to give the ransom the hackers asked.
What if you do not have enough funds to buy Bitcoin–the virtual currency used by hackers to conduct their transactions? You will end up having all your personal data deleted forever, leaked online, or worst, sold in dark web marketplaces.
New set of #ransomware discovered by security experts! Everyone beware!Click To TweetRecently, reports of a new set of ransomware that threatens the safety of everyone surfaced online. Two of the three malware spotted by security experts are not new and have been used before to stage cyber attacks.
Before WannaCry and Petya wreaked havoc globally this year and shut down hospitals, factories, banks, and other business institutions, there were the infamous ransomware Mamba and Locky.
These two old ransomware suites are making a comeback, and this time, they are back with stronger and more damaging variants than ever before. On the other hand, the other one is a new variant of ransomware dubbed by experts as EV ransomware.
The Locky Ransomware
Locky first made its presence known in 2016. It is considered one of the most largely distributed ransomware infections across the globe. According to the Hacker News, Locky can encrypt almost all kinds of file formats found on a person’s computer and network.
Locky ransomware has staged several comebacks these past months. However, security experts discovered a fresh spam malware campaign that spreads a new variant of Locky dubbed as Diablo6.
An independent researcher that goes by the Twitter username @Racco42 tweeted about the new Locky variant that appends the .diablo6 file extension after encrypting the files on an infected computer.
Microsoft Malware Protection Center (MMPC) shared a separate tweet about the said ransomware on August 9.
It appears that the Diablo6 variant comes in an email attached as Microsoft Word file. When clicked or opened, a VBS Downloader script will be executed which will attempt to download the Locky Diablo6 payload from a remote file server.
Using RSA-2048 key (AES CBC 256-bit encryption algorithm) on the targeted computer, the ransomware will then encrypt all the data. A message will be displayed on the computer screen instructing the victim to install TOR browser and visit the hacker’s website for further instructions.
Further reports stated that this new variant of Locky ransomware demands 0.49 Bitcoin or over USD 2,000 in exchange for the victim’s files. Currently, there are no known means to recover data encrypted by Diablo6, so everyone is advised to exercise caution when opening unknown email files.
Full-Disk Encrypting Ransomware: Mamba
Unlike Locky that only encrypts computer files, the malware Mamba is a different story. This ransomware is tagged by experts as so powerful and dangerous because of its capability to encrypt the entire hard disk of an infected computer.
In fact, attackers behind Petya and WannaCry have incorporated the same tactics used in Mamba. The only difference is that Mamba ransomware has been designed to destruct the computer networks of large-scale enterprises rather than extort Bitcoins from them.
Last year, it was reported that a Mamba ransomware attack had affected the operation of San Francisco’s Municipal Transportation Agency (MUNI) system’s network over Thanksgiving. The said attack resulted in major train delays and forced officials to shut down some stations.

Security experts from Kaspersky Lab spotted a new campaign spreading Mamba infection which targets large corporation in different countries such as Brazil and Saudi Arabia.
Using an open source Windows disk encryption utility called DiskCryptor, Mamba can fully encrypt computer hard drives in targeted organizations. Little is know yet about this new variant of Mamba ransomware. However, experts believe that it is being executed using an exploit kit found on malicious sites or suspicious emails.
According to Kaspersky, “there is no way to decrypt data that has been encrypted using the DiskCryptor utility because this legitimate utility uses strong encryption algorithms.”
The EV Ransomware
Unlike the Locky and Mamba ransomware which are used to encrypt computer files or workstations, EV ransomware is used to target WordPress websites. EV was discovered by the security experts from Wordfence.
In a post published in Wordfence blog site, Mark Maunder, CEO of Wordfence explained:
“Most ransomware targets Windows workstations. However, the Wordfence team is currently tracking an emerging kind of ransomware that targets WordPress websites.
During our analyses of malicious traffic targeting WordPress sites, we captured several attempts to upload ransomware that provides an attacker with the ability to encrypt a WordPress website’s files and then extort money from the site owner.”
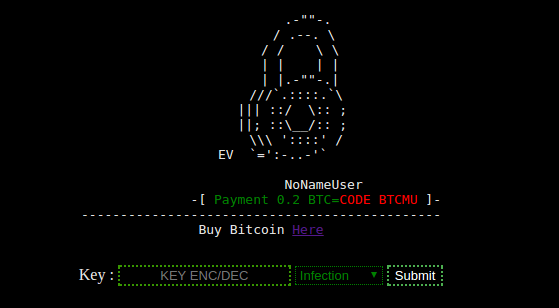
According to the post, the ransomware will not encrypt files that have the following patterns:
- *.php*
- *.png*
- *404.php*
- *.htaccess*
- *.lndex.php*
- *DyzW4re.php*
- *index.php*
- *.htaDyzW4re*
- *.lol.php*
Maunder went on to say that the “ransomware provides an attacker with the ability to encrypt your files, but it does not actually provide a working decryption mechanism. It does, however, give attackers what they need to trick affected site owners into paying a ransom. Their only goal is to encrypt your files. They don’t actually have to prove they can decrypt your files to get you to pay a ransom.”
Further investigation suggests that the attackers behind EV ransomware are of Indonesian origin. Also, the ransomware is considered incomplete since security experts found that the decryption function is not working properly.
At this stage, the ransomware is seen as effective enough to extort money from unsuspecting website owners, but without any guarantee of getting their sites decrypted. Maunder suggest that WordPress website owners secure offline backups and ensure that their backups are saved on a different web server.

















Comments (0)
Least Recent