This article details recent news about a hacker who claims to be selling Apple internal tool access.
User @XCoder8 on Twitter keeps posting about selling Apple ID info. The user claims to have access to internal Apple tools to get insider information on devices and people.
Does this “hacker” really have millions of Apple users compromised?
Still Unsure Despite Initial Reports
The short answer is no…..maybe? Results are inconclusive at this juncture in time.
So far, ZDNet has been one of the few outlets to report on this incident. But they were able to successfully contact the hacker in question for comment.
He even provided a screenshot of what his internal tool access looks like.
He has tweeted several photos, claiming they are proof of his access to Apple’s Global Service Exchange (GSX) system. This system allows authorized workers and other staff to provide after-sales support and field repair requests.
The hacker provided ZDNet with accurate information on Apple Watch serial number, model, series, and type. But the screenshots also showed the device to be “out of warranty” which was inaccurate of this Apple Watch in question.
ZDNet attempted to surmise if the hacker had access to real information or not. They did not get a straight answer from the hacker himself. But he did claim to sell access to Apple systems to around 20 people everyday using a “private exploit.”
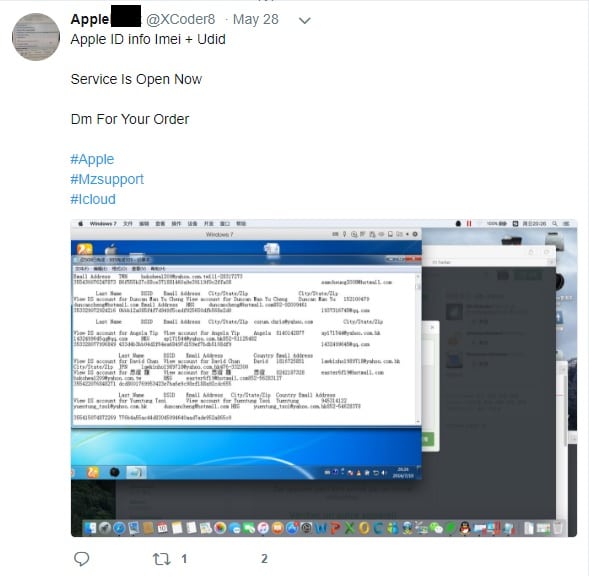
Likely a Test Version of the GSX Tool
Apple system familiars said that this tool was, likely, used for development only.
The data returned is not real, but “dummy data”, so it may have real serial numbers. But beyond that, it won’t return any actionable information.
This still doesn’t explain how the hacker obtained access to this tool in the first place.
Perhaps Apple WWDC 2018 news will shed some light on the situation (but probably not).


















Comments (0)
Least Recent