What’s the best way to secure your online privacy from prying eyes? EdgyLabs weighs in on internet security.
What’s ToR?
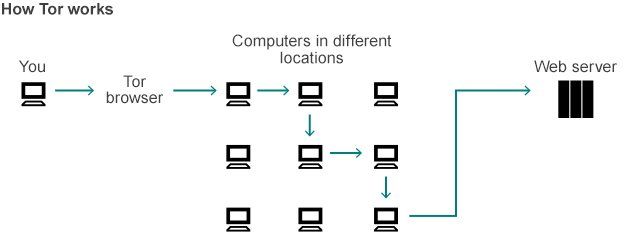
ToR stands for The Onion Router. It’s software that masks your IP address by connecting you to the internet in an atypical way. Instead of your computer identifying its IP in order to gain access to the internet, your computer is connected to many different computers across the globe. You can then interact with those other global users in various ways. In my own opinion, ToR is one of the worst methods for securing your privacy. It’s far too complex for even intermediate PC users to understand, incredibly slow, and can pose serious risks of its own–interacting with users and files via the Tor browser is like heading into a minefield.
What’s a VPN?
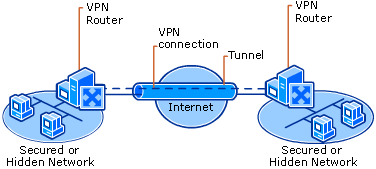
VPN stands for Virtual Private Network. A VPN securely connects your computer to another network (typically located in another country) through your existing internet. VPNs that do not save logs generally cannot see where you are or what you access. VPNs also give you an added layer of security since they encrypt your data. One good way to think about your VPN is to imagine a tunnel that passes through the Internet to connect to a secure server.
What’s a Proxy?
Proxy refers to someone who acts on the behalf of someone else. Proxy servers substitute another IP address (usually that of the proxy server) for your own. If you’re part of a large network of computers that share an internet access point (like a computer lab at the library) the administrator may have blocked you from accessing certain suspicious or inappropriate sites. If you trust that site, need to access it for research, or are unable to contact your administrator–you might consider using a proxy service.

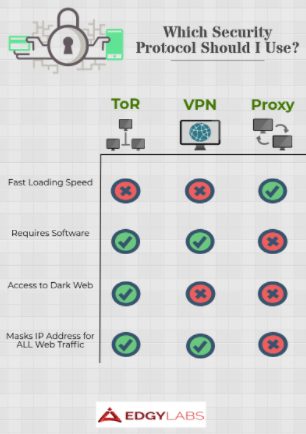
Which Service Should I be Using?
People use ToR, VPN, and Proxies for a huge number of reasons–illegal activity typically isn’t one of them. These services can help you browse the web more securely and more deeply than your default browser. To help you understand which service will work best for you, carefully consider why you’re interested in this type browsing and what devices you plan to use.
I frequently use mobile devices or home wifi:
If you use mobile devices or home wifi, your best option is to install a VPN client that does not retain logs of your activities. Personally, I think Hide.me provides a great free service that’s as quick as it is to install as it is to browse with.
I want to access the Dark Web:
The “Dark Web” can only be accessed through an Onion router like ToR. Please be advised: It’s a completely different way of accessing the Internet and can be very dangerous.
I want my credit card information to be safe when I shop online:
You can use either a VPN or Proxy, but I personally find it easier and faster to simply leave a VPN turned on rather than to manually enter every website I’d like to visit.
I want to browse the web without having to worry about my personal data being sold to advertisers:
Both VPN and Proxy services can assist with this. Choose which option works best for you based on your browsing habits.
I want to get past web restrictions that are specific to my location (office, school, etc):
Especially since these kinds of computers often have restrictions on what kinds of software you have the authorization to download, a Proxy will be your best bet.
I want to protect my home/office against doxxing attacks:
Use a VPN to ensure no site you visit collects information about your location. Be sure to reflect on your other online habits (esp.: social site activities like sharing photos) to see if you can prevent the most basic types of attacks first.



















tuxler vpn can give a user an access to the dark web
I would not make a choice of any VPN without first reading user reviews on vpnMentor, the only site that you can get honest user reviews and not just fake complements on the vpns that pay advertising money