A Parity vulnerability discovered yesterday froze over $150 million USD worth of Ethereum.
Parity Technologies, a company popularly known for its multi-sig Ethereum wallet service, announced on Tuesday an issue in its system that could potentially wipe all the contents of a wallet. The alleged Parity vulnerability caused millions of dollars in Ethereum funds to be frozen.
The new Parity issue is the second flaw to be discovered following the first Parity breach reported in July that led to the hacking of over $30 million USD worth of Ethereum.
According to Security Alert issued by Parity Tech yesterday, the vulnerability was found in the Parity wallet library contract of the standard multi-sig contract. Multi-sig contracts or wallets make use of a technology that uses the consent of multiple parties to secure all transactions within the blockchain.
Affected users include those with assets in multi-sig wallets created in Parity wallets that were deployed after July 20th of this year.
@ParityTech announced a vulnerability that froze millions worth of #EthereumClick To TweetThe Parity Vulnerability
Users of Parity wallets were confused yesterday after the company revealed the discovery of the security threat. Tagged as critical, the alleged Parity vulnerability rendered all multi-sig contracts inaccessible-effectively locking up millions of dollars in Ethereum in order to ensure its security until the vulnerability was addressed.
The threat was said to have been discovered accidentally by Parity. A part of the advisory released by company read:
“It would seem that issue was triggered accidentally 6th Nov 2017 02:33:47 PM +UTC and subsequently a user suicided the library-turned-into-wallet, wiping out the library code which in turn rendered all multi-sig contracts unusable since their logic (any state-modifying function) was inside the library.”

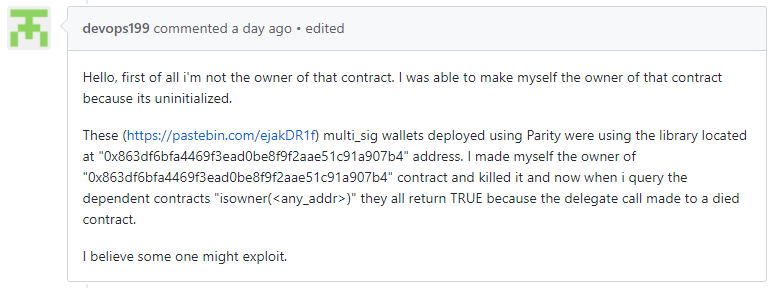
A certain Ethereum user that goes by the handle devops199 claimed that he made himself the owner of a contract which he later ‘killed’ accidentally by removing a critical element of the library code. In an issue opened on GitHub, devops199 said:
“I’m not the owner of that contract. I was able to make myself the owner of that contract because it’s uninitialized. These (https://pastebin.com/ejakDR1f) multi_sig wallets deployed using Parity were using the library located at “0x863df6bfa4469f3ead0be8f9f2aae51c91a907b4” address.
I made myself the owner of “0x863df6bfa4469f3ead0be8f9f2aae51c91a907b4” contract and killed it and now when i query the dependent contracts “isowner()” they all return TRUE because the delegate call made to a died contract.
I believe someone might exploit.”
The issue now appears to center around the fact that Parity operates using smart contracts.
Early estimates by cryptocurrency experts such as Patrick McCorry suggest that the amount of frozen Ethereum cost around $150 million USD.
McCorry told TechCrunch that the amount is likely to be higher as more information and wallet volumes come to light. While there are no reports of stolen or lost coins, it is still clear that sizable amount of Ethereum is at risk.
With the vast amount of funds frozen in the multi-sig wallets, many investors are now calling for a hard fork to bailout the frozen funds. Apparently, pointing the funds to a newly deployed library and updating deployed wallets won’t work without a fork.
While Parity said that they are exhausting all resources to find a fix to the issue, it appears that only a hard fork could put back the library contract in an initialized state.
No one knows for sure what devops199’s intentions are for killing the contract. Some speculate that he’s a hacker trying to replicate the July Parity hacking incident.
Right now, all Parity wallet users are left with no option but to wait.


















Comments (0)
Most Recent