Apple is currently facing a ‘potential’ threat to its mobile iOS security as a hacker releases to the public what he claims to be the full decryption key of the Secure Enclave security chip.
In a tweet, yesterday afternoon, the hacker that goes by the handle @xerub tweeted links related to the full decryption keys of Apple’s Secure Enclave Processor firmware.
In a report from Threatpost, @xerub said that the key only unlocks the SEP firmware and it would have no impact on user data. He went on to say that “everybody can look and poke at SEP now.”
@xerub released decryption keys of #Apple 's Secure Enclave Processor!Click To TweetWhat is Secure Enclave?
The Secure Enclave is a security chip or coprocessor located inside the mobile operating system of iPhones equipped with A7 Chip. Its functions include processing fingerprint data from the Touch ID sensor, determining matches against registered fingerprints, and enabling access or purchases on behalf of the mobile phone owner.
Simply put, the Secure Enclave processor or SEP firmware is in charge of securing an Apple mobile phone. According to the iOS Security Guide, SEP uses encrypted memory and includes a random number generator.
“The Secure Enclave is a coprocessor fabricated in the Apple S2, Apple A7, and later A-series processors. It uses encrypted memory and includes a hardware random number generator.
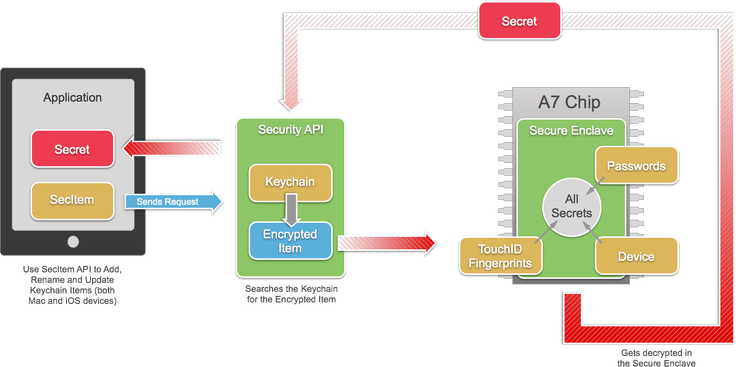
The Secure Enclave provides all cryptographic operations for Data Protection key management and maintains the integrity of Data Protection even if the kernel has been compromised. Communication between the Secure Enclave and the application processor is isolated to an interrupt-driven mailbox and shared memory data buffers.”
The iOS Security Guide also stated that Secure Enclave “provides all the cryptographic operations for Data Protection key management and maintains the integrity of Data Protection even if the kernel has been compromised.”
What’s the Deal now That Secure Enclave Decryption Key has Been Leaked?
While the user data of iPhone owners are not at risk of being compromised, the decryption key exposes the SEP firmware to unauthorized researchers and ‘possible’ attackers alike. It opens the door for the said firmware to be studied and exploited.
According to a post from TechRepublic, xerub said:
“The fact that [the SEP] was hidden behind a key worries me. Is Apple not confident enough to push SEP decrypted as they did with kernels past iOS 10? Obscurity helps security—I’m not denying that.”
He went on to say that his intention is to make SEP more secure in the long run.
“I think public scrutiny will add to the security of SEP in the long run. Apple’s job is to make [SEP] as secure as possible. It’s a continuous process … there’s no actual point at which you can say ‘right now it’s 100% secure.”
An Apple insider who wishes to remain unidentified confirmed that the release of SEP key would not compromise user data.
“There are a lot of layers of security involved in the SEP, and access to firmware in no way provides access to data protection class information.”
Apparently, the Secure Enclave processor can be infiltrated by using @xerub’s img4lib to decrypt the firmware and the SEP firmware split tool to process it. Apple has not given any official statement yet about the matter.



















Comments (0)
Most Recent