Security researchers are warning Android users against a recently discovered Google Play Store Malware that could allegedly sidestep an advanced security feature.
The malware-carrying Android apps are said to be capable of accessing one-time passwords sent through SMS two-factor authentication (2FA) messages without any permission. This new technique not only circumvents Google’s restrictions on the use of SMS and Call Log permissions, but it also steals OTPs sent via email-based 2FA systems.
ESET discovered the security threat on some apps available for download on Google Play Store earlier this month and reported it to Google. Lukas Stefanko, a malware researcher at ESET, explained:
“The apps impersonate the Turkish cryptocurrency exchange BtcTurk and phish for login credentials to the service. Instead of intercepting SMS messages to bypass 2FA protection on users’ accounts and transactions, these malicious apps take the OTP from notifications appearing on the compromised device’s display. Besides reading the 2FA notifications, the apps can also dismiss them to prevent victims from noticing fraudulent transactions happening.”
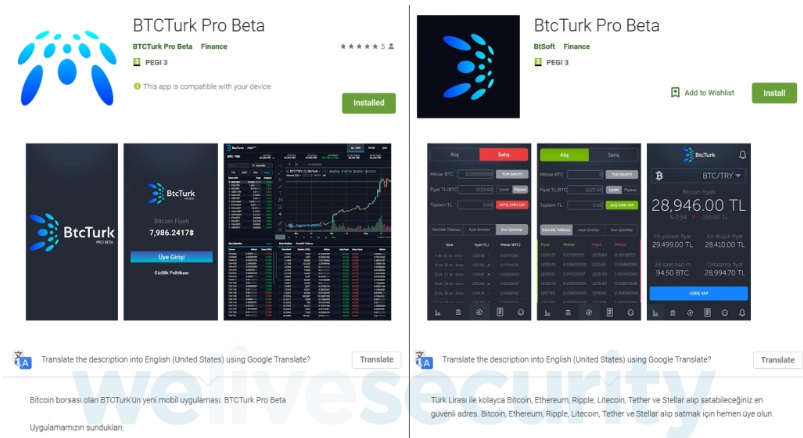
Malicious Google Play Store Apps
According to Stefanko, the first of the many apps containing the new Google Play Store malware was uploaded last June 7th. The malicious app was called BTCTurk Pro Beta under developer ‘BTCTurk Pro Beta,’ which was developed to mimic the Turkish cryptocurrency exchange firm BtcTurk.
It should be noted that BtcTurk’s mobile app is registered as BtcTurk Bitcoin Borsası on Google Play Store and is only available for download in Turkey. ESET immediately reported BTCTurk Pro Beta to Google, but at the time of reporting, it’s already been downloaded over 50 times.
Stefanko further reported that the next malicious app was uploaded on June 11th as BtcTurk Pro Beta under the developer ‘BtSoft.’ The researcher noted that while the two apps greatly resembled each other, they seemed to be uploaded by two different attackers. The other app was reported to Google last June 12th.
As soon as the 2nd malware was removed from the Play Store, the same attacker uploaded another app under the name of BTCTURK PRO, containing the same screenshots and icons. ESET reported the third app on June 13th to Google.
How the new Google Play Store Malware Works
The Google Play Store malware works by requesting specific permission labeled as Notification access as soon as the user launched the infected app. The permission enables the malicious app to read the notifications displayed by other apps installed on the same device. Then, it either dismisses the said notifications or clicks the buttons they contain without the knowledge of the user.

Google introduced the Notification access permission to all Android devices starting on version 4.3 (Jelly Bean) up to the present. All Android apps at the moment are required to run this feature, making over 90 percent of Android devices potential targets.
After granting permission to the fake app, it will display a fake login form asking users to enter their BtcTurk credentials. Once the username and password have been entered, a Turkish error message will be displayed citing that the service for the mobile app is temporarily unavailable.
“Opss! Due to the change made in the SMS Verification system, we are temporarily unable to service our mobile application. After the maintenance work, you will be notified via the application. Thank you for your understanding.”

After this whole process has been completed, the malware will now be able to read all notifications, including SMS and emails, from other apps. Stefanko explained that the malicious apps only target notifications containing keywords “gm, yandex, mail, k9, outlook, SMS, messaging.”
The content of the notification is then sent to the attacker’s server where they can freely access them regardless of the security settings used by victims on their Android devices. While this new technique can prevent mobile users from knowing fraudulent transactions by blocking notifications, the 2FA bypass has its limitations.
“As for effectiveness in bypassing 2FA, the technique does have its limitations – attackers can only access the text that fits the notification’s text field, and thus, it is not guaranteed it will include the OTP.”
ESET found another malicious app that utilizes the same technique uploaded last week on Google Play Store. The app was said to be uploaded by the developer of the BTCTurk Pro Beta and resembled another Turkish cryptocurrency exchange firm called Koineks.
Stefanko warns Android users to stay safe by uninstalling suspicious apps immediately and by regularly checking accounts for any fraudulent activities.


















Comments (0)
Most Recent